Multi-site PBX Connectivity in ACME SBC
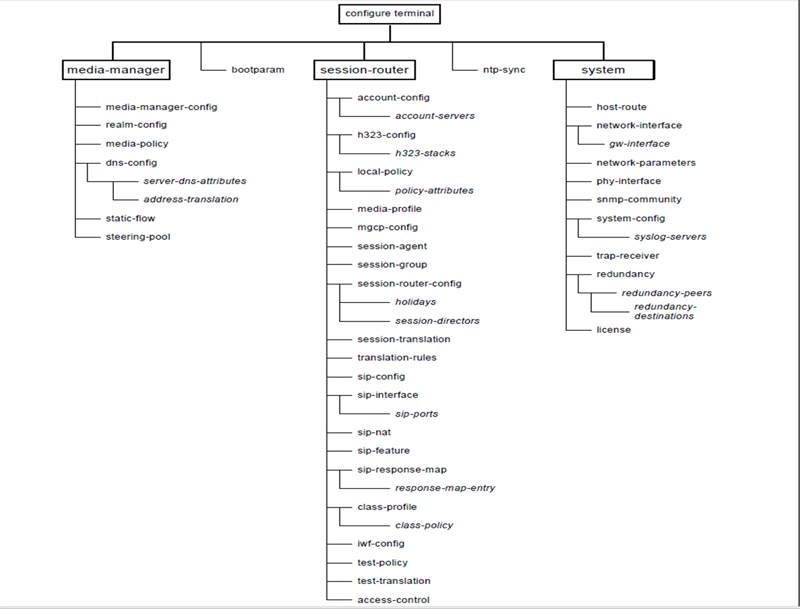
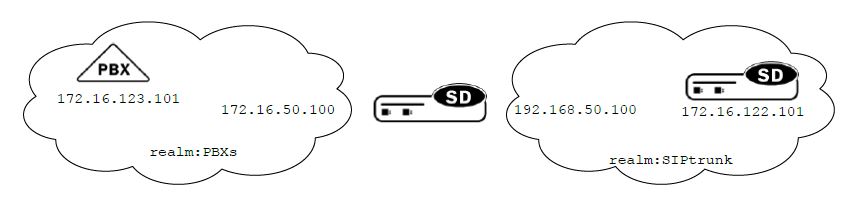
Multi-site PBX Connectivity in ACME SBC : Consider the scenario where the Enterprise has multiple branch offices, each with one or more PBXs deployed. Should there be an ACME Net-Net SD on the network edge of each of the branch offices, then the Basic PBX Connectivity approach in the section above should be used at each office location.
However, should the ACME Net-Net SD be deployed in a data center as an aggregation point for many or all branch offices, then a multi-realm approach is recommended.
Typically, routing per branch office would be on a separate VLAN id. There is a one-to-one correlation of VLAN id and realm. Additionally, there is a one-to-one correlation of realm and sip-interface. Hence, the simplest model of multi-site PBX connectivity would require the Net-Net SD be configured with as […]